Information Security Principles of Zone Media OÜ
General provisions
The mission of Zone is to provide simple, fast and reliable solutions for transmission of and processing of information on the Internet.
Information security has a critical role to play in achieving the mission of our company, and the management and employees of Zone are committed to maintaining the confidentiality, integrity and availability of the information assets of the company and its clients.
For example, in the processing of personal data, we have two equally important roles – depending on the context we can be the controller or the processor of personal data.
Within the context of the General Personal Data Regulation, our main task is to implement sufficient technical and organisational security measures for our services and infrastructure (hosting space, servers, network equipment, etc) to ensure that the data processed by the clients will be protected against accidental or unlawful deletion, unauthorised access or disclosure.
This information leaflet is to provide you an overview of what to do to ensure the security of the data processed in our infrastructure (including personal data).
It is of utmost importance that you examine this leaflet, as Regulation 2016/679 of the European Parliament and of the Council (the General Data Protection Regulation) sets forth the following:
If personal data are processed on behalf of the controller, the controller shall use only processors providing sufficient guarantees to implement technical and organisational measures in such manner that the processing will meet the requirements of the Regulation and the protection of the rights of the data subject is ensured therewith.
The controller – it means you. You will have to make sure that we as the processor will protect our organisation, services and infrastructure (hosting space, hardware, software, data communication networks and other resources) in accordance with the requirements of laws and the best practices of the industry. You will naturally also have to know what your duties and responsibilities are upon the processing of personal data.
Nature of services
Let us start with the general description of our services.
While using our services, you should remember that we provide a major part of our services as universal could services to our clients. It means that these services are not by default adapted individually to you, but meet the general demands of the market. Individual agreements and adaptions are still possible.
As a cloud service provider, we have no control over the data that you upload to our infrastructure or process therein. It means that we do not know by default whether out services are used for the processing of personal data, which personal data are being processed and whether such processing is lawful. If necessary, you yourself will have to evaluate the effect of data processing and its conformity to applicable laws.
Service classes
The majority of the services offered by Zone are classified as cloud services. They are based on the following main cloud service models:
- ‘Software as a Service’ (SaaS) delivers the ready-to-use application to the client;
- ‘Platform as a Service’ (PaaS) provides conditions necessary for managing an application;
- ‘Infrastructure as a Service’ (IaaS) offers virtual servers to the client for creating one’s own platform.
The scope of the duties of Zone and of the client vary within the framework of these models in accordance with the chosen service. We have also described it in the leaflet of our every service under the section “Division of responsibility”.
The following drawing provides a general overview:
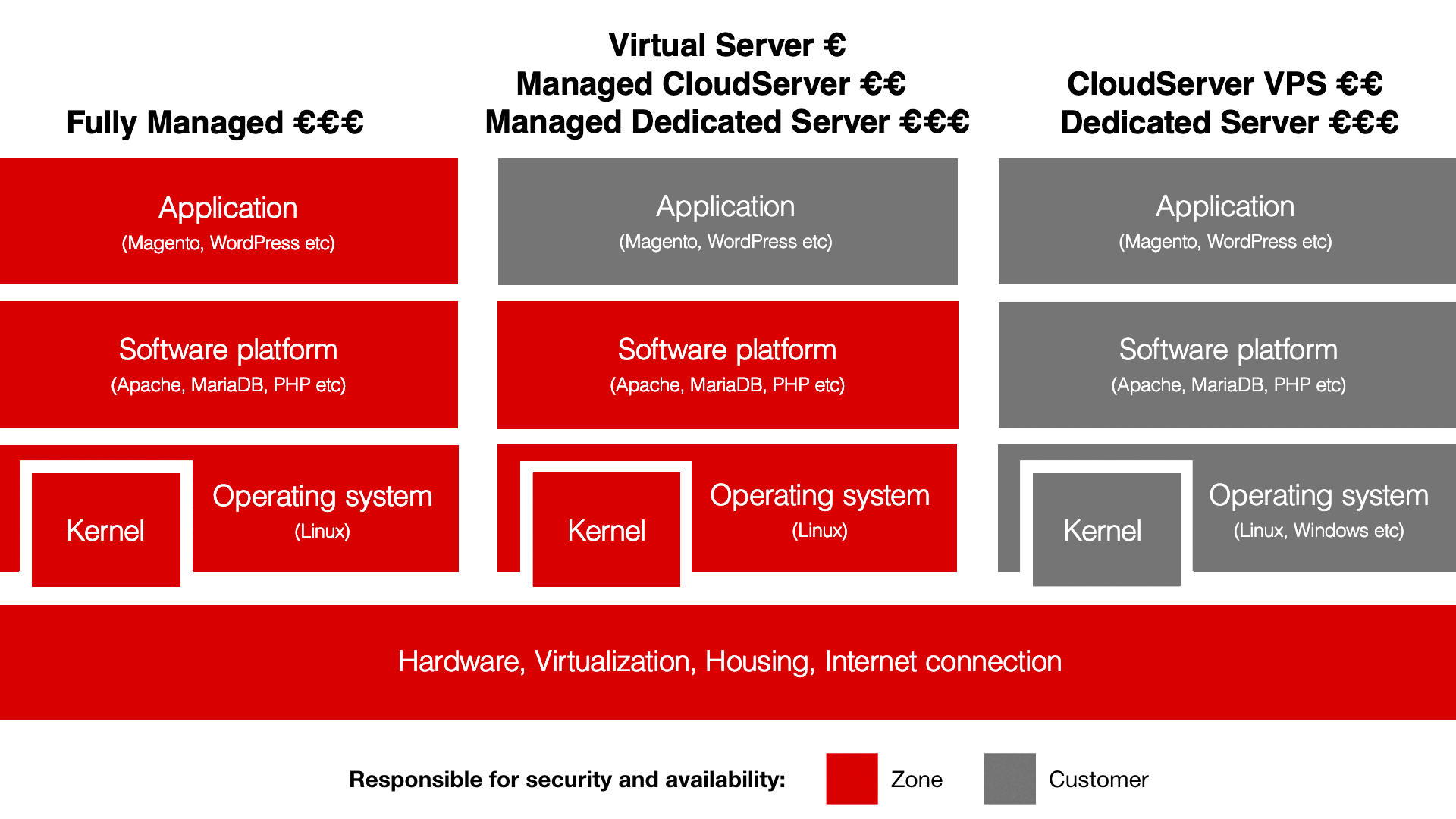
The e-mail, DNS and ZoneCloud included in the virtual server service are SaaS services and the responsibility of Zone extends also to the application layer.
It is important to remember that the security of access data, applications and transport of data is almost always in the sphere of responsibility of the client by default.
Service delivery models
Three service delivery models are in use:
- Joint use;
- Individual use;
- Hybrid use.
Joint use means that several organisations share the same servers. Services such as the Virtual Server, Cloud Server VPS, Cloud Server Pro and Smart Cloud Server are based on joint use. These services cost less, but they involve also greater risks than individual use – the additional risks are mainly connected with the other users of the service.
For example, in case of joint use there is a possibility that a client may with excessive use of resources negatively affect the availability of the websites of other clients. Zone has a long experience in offering services based on joint use, and the means for mitigating such risk are already included in our software platform, but it is not possible to eliminate the risks relating to availability of resources within 100% in the jointly used environment.
In case of individual use, servers are only at the disposal of one client. Individual use is applied in case of the Private Server and partially also the Smart Private Server services, whereby a client receives guaranteed private server resources to its use. In case of individual use, the client does not share the server resources with other clients which will substantially mitigate the risks related to the availability of the service and confidentiality of data. In addition, the individual use enables to implement client-based information security measures to the server(s) as necessary.
The main advantage of individual use is that in case of a potential incident, the restoration of the service to the given client shall be a priority. In case of joint use, the interests of the majority of clients shall be of main importance. The minor disadvantage of the individual use is its higher price.
In case of hybrid use, different models may be used for different components of the service. The hybrid model is applied by default to the Smart Private Server service, where the server servicing web applications and database are dedicated only to one client, but the e-mail and DNS services share resources with other clients. In case of special solutions, this division may naturally vary – we will also be able to offer private e-mail servers, etc upon request.
Information security at Zone
Information security process and organisation
It is of primary importance that the organisation shall be devoted to information security. For this purpose, our management has established the Information Security Policy which is implemented all over our company – adherence to the established principles is expected from the managers, employees and also from the contractors of Zone, as they participate in the operations of our company. The up-to-dateness of the policy is assessed at least once a year.
The Information Security Officer is responsible for the preparation, supplementing and implementation of the Information Security Policy.
The Information Security Officer is supported in his work by a broad-based information security team and the Data Protection Officer. All the structural units and employees are naturally engaged in the information security process.
We have developed our Information Security Policy in accordance with the standard ISO/IEC 27001:2014 and our goal for the future is to reinforce our conformity to the standard by undergoing also the official certification process.
Zone shall administer information security risks based on the recommendations of the standard ISO/IEC 27005:2014 and shall use the qualitative asset-based risk weighting methods.
Security level of the client’s information assets
The client is the responsible owner of the client’s information assets (files, databases, e-mails, etc) stored and processed in the IT systems of Zone.
The security level of the client’s information assets in our internal systems is ‘confidential’ which is defined as follows: the use of information is allowed only for certain specific groups of users, access to information is permitted in case of legitimate interest of the person seeking access (e.g. if it is necessary for performance of work duties).
The internally applicable security level of Zone is not automatically transferred outside the company. The client has to store, process and transfer his or her information in the IT systems of Zone in accordance with the security levels given by the Client to his or her own information assets, as well as weighted risks, and organise implementation of security measures accordingly.
We never sell any data uploaded to the infrastructure of Zone, uploaded by the client’s users or created in the server in the course of the use of the service by the client to anyone, and we shall not use such data without the client’s permission in our own direct economic interests. Zone shall process such data only to the extent required for providing its services or user support related thereto.
Personal data protection at Zone
In order to carry out supervision over personal data protection, we have created the position of a Data Protection Officer, and the person holding this position has undergone also the training programme recognised by the Data Protection Inspectorate.
We maintain records of the processed personal data as well as of the effect of processing on such data.
Further information on personal data processing is available in the Privacy Policy of Zone Media OÜ.
Location of data
We provide our services in physically safe conditions. The data centres used by Zone are located in the territory of the European Union.
For the purpose of hedging information security, durability and business risks and for offering unique opportunities to our clients, our infrastructure is distributed among 5 data centres, 4 whereof are located in Tallinn, Estonia, and 1 is located in Amsterdam, Holland. In infrastructure hosting, Zone co-operates with the acknowledged partners such as Equinix, Linxtelecom, Telia and Elisa.
The data centres used by Zone are located in the buildings constructed or adapted specially for the hosting of information and communication technology equipment and are separated from public space. The equipment is located in premises separated by security fence or in locked equipment cabinets. Access is limited with the persons who have a need for access deriving from their work duties.
Data centres are equipped with security cameras and alarm systems, and a log is maintained regarding entry to the centres. The centres use an automated fire alarm system and automated gas fire extinguishing system.
In order to maintain the temperature and relative air humidity at the level suitable for servers and data communication equipment, all the data centres have cooling equipment and systems.
In order to ensure more reliable power supply, all the equipment of Zone is connected to uninterruptible power supply (UPS) and the buildings have power generators.
In order to ensure availability, all the data centres have redundancy of equipment and technical systems.
The areas where the buildings used by Zone are located are not exposed to any significant risks related to weather or local geology, and no damage has been previously caused to the data centres by these circumstances.
Data communication
In order to mitigate the risks related to information security, durability and business and to provide unique opportunities to its clients, Zone co-operates with several reliable telecommunication companies. The data communication partners of Zone are Cogent Communications, Level3 Communications, Linxtelecom, Telia and Elisa.
In Estonia, Zone uses parallelly three and in Holland we use two Internet transit connections – the redundancy of connections ensures that the clients have connectivity even during a single connection failure or maintenance work.
Zone has established a unique private regional network between Estonian hosting centres with the purpose of additional management of risks to the availability of services deriving from external conditions. The data centres providing server services are connected to two other centres at the same time – the resulting network setup enables to maintain connectivity at the centre even during a failure or maintenance of one connection.
In addition, Zone is connected with many telecommunications companies and companies providing Internet services in Estonia by two major Internet exchange points of Estonia – TLLIX and RTIX.
Zone will make sure that in normal circumstances the transmission connections would be underutilised and additional resources would be readily available as necessary.
In order to manage specific risks deriving from denial of service attacks, Zone has equipped its Internet connections with special equipment mitigating the negative impact of attacks.
Backup of data
Zone shall make backup copies of servers related to the services administered by Zone, based on the following rules:
- a backup copy of the files, SQL databases and mailboxes in a web server shall be made at least once a day;
- a backup copy shall be usable for restoring any backed-up data for at least 14 days after the moment when the backup copy was made;
- backup copies shall be made, as necessary, before major software updates or modifications which may endanger the integrity of data.
We store backup copies of the servers used for providing the services administered by Zone separately from the production environment.
In case of services based on individual use, it is possible to adapt the backup policy to the client’s needs.
As a client, you will have to take into account that the time of restoring of data depends directly on the nature and volume of data, and in case of joint use, it is also affected by other clients using the same resource.
Monitoring
Zone shall monitor the work of the servers providing the services 24 hours a day and 7 days a week.
Among other things, Zone monitors any references to the compromising of the platform or the client’s services, including the start of unknown processes, opening of unexpected network ports, activity of users, sending of spam, etc.
Active monitoring takes place from 08.30-17.30 on business days. In case of active monitoring the employees of Zone Media monitor the output of the monitoring system in real time, and in addition, the monitoring system informs the technicians of Zone via mobile communication network. Incidents are responded to without delay.
Passive monitoring takes place from 17.30-08.30 on business days and 24 hours during weekends. In case of passive monitoring, the monitoring system informs Zone’s technician on call about any problems via mobile communication network. The technician on call shall respond to incidents without delay.
Client support
The working hours of Zone’s telephone support and e-mail support is from 09.00 – 17.00 on business days (time zone EET/EEST).
The client support telephone number is: +372 688 6886
The client support e-mail address is: info@zone.ee
Should you have any questions regarding personal data processing, you may contact directly the Data Protection Officer of Zone at the address dataprotection@zone.ee.
The current update of the service platform of Zone is available on the website http://status.zone.eu.
E-mails sent outside the working hours are handled by the team on call which shall organise response to any critical incidents.
The 24/7 helpline is available to the clients of services based on individual use, as necessary, which is meant for notification of critical incidents.
Processors engaged by Zone
We may engage processors in the processing of a client’s data.
We do it only if we are sufficiently certain that they implement appropriate technical and organisational measures in such manner that the processing of data is in compliance with the requirements set out by law.
We publish the list of significant processors engaged in the processing of clients’ data on our website (https://www.zone.ee/et/lepingud/volitatud-tootlejad/).